02-05-2023, 09:44 PM
Ever wanted to give someone a timed trial of your program? Let them download it, play around for a few days, and then pop up a nag screen telling them to buy your junk? Well, now you can!!
First the timestamper!
And, a program set up to showcase the basic workings of it:
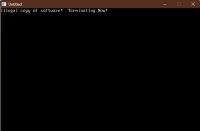
So, to start with, run the second file first. It'll make an EXE for you and tell you that it's illegal! You're not allowed to use it. This is all someone that grabs your program out of the blue will see.
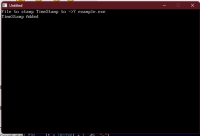
Now, if you want to send someone a timestamped trial version, run the first program and point it to your other program's compiled EXE. It'll stick a timestamp to the end of it for you, and now you can now run that EXE and have it make use of that timestamp however you want.
If they buy your junk, send (or change) the last 2 bytes of the EXE to "VC" for "Verified Copy", and they're good to go without any message for illegal downloading or nag screen to buy your stuff.
Screenshots follow:
First the timestamper!
Code: (Select All)
INPUT "File to stamp TimeStamp to =>"; file$
OPEN file$ FOR BINARY AS #1
filesize = LOF(1)
DIM TS AS _FLOAT
TS = TimeStamp(DATE$, TIMER)
PUT #1, filesize + 1, TS
t$ = "TS"
PUT #1, , t$
CLOSE #1
PRINT "TimeStamp Added"
SLEEP
SYSTEM
FUNCTION TimeStamp## (d$, t##) 'date and timer
'Based on Unix Epoch time, which starts at year 1970.
DIM l AS _INTEGER64, l1 AS _INTEGER64, m AS _INTEGER64
DIM d AS _INTEGER64, y AS _INTEGER64, i AS _INTEGER64
DIM s AS _FLOAT
l = INSTR(d$, "-")
l1 = INSTR(l + 1, d$, "-")
m = VAL(LEFT$(d$, l))
d = VAL(MID$(d$, l + 1))
y = VAL(MID$(d$, l1 + 1))
IF y < 1970 THEN 'calculate shit backwards
SELECT CASE m 'turn the day backwards for the month
CASE 1, 3, 5, 7, 8, 10, 12: d = 31 - d '31 days
CASE 2: d = 28 - d 'special 28 or 29.
CASE 4, 6, 9, 11: d = 30 - d '30 days
END SELECT
IF y MOD 4 = 0 AND m < 3 THEN 'check for normal leap year, and we're before it...
d = d + 1 'assume we had a leap year, subtract another day
IF y MOD 100 = 0 AND y MOD 400 <> 0 THEN d = d - 1 'not a leap year if year is divisible by 100 and not 400
END IF
'then count the months that passed after the current month
FOR i = m + 1 TO 12
SELECT CASE i
CASE 2: d = d + 28
CASE 3, 5, 7, 8, 10, 12: d = d + 31
CASE 4, 6, 9, 11: d = d + 30
END SELECT
NEXT
'we should now have the entered year calculated. Now lets add in for each year from this point to 1970
d = d + 365 * (1969 - y) '365 days per each standard year
FOR i = 1968 TO y + 1 STEP -4 'from 1968 onwards,backwards, skipping the current year (which we handled previously in the FOR loop)
d = d + 1 'subtract an extra day every leap year
IF (i MOD 100) = 0 AND (i MOD 400) <> 0 THEN d = d - 1 'but skipping every year divisible by 100, but not 400
NEXT
s## = d * 24 * 60 * 60 'Seconds are days * 24 hours * 60 minutes * 60 seconds
TimeStamp## = -(s## + 24 * 60 * 60 - t##)
EXIT FUNCTION
ELSE
y = y - 1970
END IF
FOR i = 1 TO m 'for this year,
SELECT CASE i 'Add the number of days for each previous month passed
CASE 1: d = d 'January doestn't have any carry over days.
CASE 2, 4, 6, 8, 9, 11: d = d + 31
CASE 3 'Feb might be a leap year
IF (y MOD 4) = 2 THEN 'if this year is divisible by 4 (starting in 1972)
d = d + 29 'its a leap year
IF (y MOD 100) = 30 AND (y MOD 400) <> 30 THEN 'unless..
d = d - 1 'the year is divisible by 100, and not divisible by 400
END IF
ELSE 'year not divisible by 4, no worries
d = d + 28
END IF
CASE 5, 7, 10, 12: d = d + 30
END SELECT
NEXT
d = (d - 1) + 365 * y 'current month days passed + 365 days per each standard year
FOR i = 2 TO y - 1 STEP 4 'from 1972 onwards, skipping the current year (which we handled previously in the FOR loopp)
d = d + 1 'add an extra day every leap year
IF (i MOD 100) = 30 AND (i MOD 400) <> 30 THEN d = d - 1 'but skiping every year divisible by 100, but not 400
NEXT
s## = d * 24 * 60 * 60 'Seconds are days * 24 hours * 60 minutes * 60 seconds
TimeStamp## = (s## + t##)
END FUNCTIONAnd, a program set up to showcase the basic workings of it:
Code: (Select All)
TYPE SYSTIME
year AS INTEGER
month AS INTEGER
weekday AS INTEGER
day AS INTEGER
hour AS INTEGER
minute AS INTEGER
second AS INTEGER
millis AS INTEGER
END TYPE
DECLARE DYNAMIC LIBRARY "Kernel32"
SUB GetSystemTime (lpSystemTime AS SYSTIME)
SUB GetLocalTime (lpSystemTime AS SYSTIME)
END DECLARE
AppendTimeStamp
SUB AppendTimeStamp
DIM AS _FLOAT TS
f = FREEFILE
OPEN COMMAND$(0) FOR BINARY AS #f
FileSize = LOF(f)
check$ = " "
GET #f, FileSize - 1, check$
SELECT CASE UCASE$(check$)
CASE "VC" 'verified copy. All is good
PRINT "You have a paid copy of this software. All is good, kindly feel free to carry on with your existence, puny human."
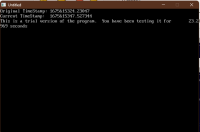
CASE "TS" 'already has a timestamp, is a limited time test version. Toss NAG Screen.
GET #1, FileSize - 33, TS
PRINT "Original TimeStamp:"; TS
PRINT "Current TimeStamp: "; TimeStamp(DATE$, TIMER)
PRINT USING "This is a trial version of the program. You have been testing it for ###,####.#### seconds"; TimeStamp(DATE$, TIMER) - TS
CASE ELSE 'first run.
PRINT "Illegal copy of software! Terminating Now!"
SLEEP
SYSTEM
END SELECT
CLOSE #f
END SUB
FUNCTION TimeStamp## (d$, t##) 'date and timer
'Based on Unix Epoch time, which starts at year 1970.
DIM l AS _INTEGER64, l1 AS _INTEGER64, m AS _INTEGER64
DIM d AS _INTEGER64, y AS _INTEGER64, i AS _INTEGER64
DIM s AS _FLOAT
l = INSTR(d$, "-")
l1 = INSTR(l + 1, d$, "-")
m = VAL(LEFT$(d$, l))
d = VAL(MID$(d$, l + 1))
y = VAL(MID$(d$, l1 + 1))
IF y < 1970 THEN 'calculate shit backwards
SELECT CASE m 'turn the day backwards for the month
CASE 1, 3, 5, 7, 8, 10, 12: d = 31 - d '31 days
CASE 2: d = 28 - d 'special 28 or 29.
CASE 4, 6, 9, 11: d = 30 - d '30 days
END SELECT
IF y MOD 4 = 0 AND m < 3 THEN 'check for normal leap year, and we're before it...
d = d + 1 'assume we had a leap year, subtract another day
IF y MOD 100 = 0 AND y MOD 400 <> 0 THEN d = d - 1 'not a leap year if year is divisible by 100 and not 400
END IF
'then count the months that passed after the current month
FOR i = m + 1 TO 12
SELECT CASE i
CASE 2: d = d + 28
CASE 3, 5, 7, 8, 10, 12: d = d + 31
CASE 4, 6, 9, 11: d = d + 30
END SELECT
NEXT
'we should now have the entered year calculated. Now lets add in for each year from this point to 1970
d = d + 365 * (1969 - y) '365 days per each standard year
FOR i = 1968 TO y + 1 STEP -4 'from 1968 onwards,backwards, skipping the current year (which we handled previously in the FOR loop)
d = d + 1 'subtract an extra day every leap year
IF (i MOD 100) = 0 AND (i MOD 400) <> 0 THEN d = d - 1 'but skipping every year divisible by 100, but not 400
NEXT
s## = d * 24 * 60 * 60 'Seconds are days * 24 hours * 60 minutes * 60 seconds
TimeStamp## = -(s## + 24 * 60 * 60 - t##)
EXIT FUNCTION
ELSE
y = y - 1970
END IF
FOR i = 1 TO m 'for this year,
SELECT CASE i 'Add the number of days for each previous month passed
CASE 1: d = d 'January doestn't have any carry over days.
CASE 2, 4, 6, 8, 9, 11: d = d + 31
CASE 3 'Feb might be a leap year
IF (y MOD 4) = 2 THEN 'if this year is divisible by 4 (starting in 1972)
d = d + 29 'its a leap year
IF (y MOD 100) = 30 AND (y MOD 400) <> 30 THEN 'unless..
d = d - 1 'the year is divisible by 100, and not divisible by 400
END IF
ELSE 'year not divisible by 4, no worries
d = d + 28
END IF
CASE 5, 7, 10, 12: d = d + 30
END SELECT
NEXT
d = (d - 1) + 365 * y 'current month days passed + 365 days per each standard year
FOR i = 2 TO y - 1 STEP 4 'from 1972 onwards, skipping the current year (which we handled previously in the FOR loopp)
d = d + 1 'add an extra day every leap year
IF (i MOD 100) = 30 AND (i MOD 400) <> 30 THEN d = d - 1 'but skiping every year divisible by 100, but not 400
NEXT
s## = d * 24 * 60 * 60 'Seconds are days * 24 hours * 60 minutes * 60 seconds
TimeStamp## = (s## + t##)
END FUNCTIONSo, to start with, run the second file first. It'll make an EXE for you and tell you that it's illegal! You're not allowed to use it. This is all someone that grabs your program out of the blue will see.
Now, if you want to send someone a timestamped trial version, run the first program and point it to your other program's compiled EXE. It'll stick a timestamp to the end of it for you, and now you can now run that EXE and have it make use of that timestamp however you want.
If they buy your junk, send (or change) the last 2 bytes of the EXE to "VC" for "Verified Copy", and they're good to go without any message for illegal downloading or nag screen to buy your stuff.
Screenshots follow: